How re-signing up for an account lead to account takeover
This is a quick write-up about an interesting bug I found on a bounty program which lead to unauthorised access to any account you knew the email of (no password needed!). I believe some other researchers may of overlooked the functionality of the site and some of the requests that were made.
Tip: when testing a site you will be surprised at how many act different depending on user agent,device,language, session (logged in/out). When testing you should test from as many different angles as possible to check if anything is different / discover new endpoints. Some responses will display different links, ads, sections of the site, etc.
It’s all in the detail
With the tip above in mind, I decided to signup for an account on this site and went through all the steps to verify it. After signing up I will always simply re-visit the signup page because sometimes if it renders, entering another users email / changing some details can lead to unexpected results (another post another time :D).
In this case, upon re-visiting the signup page it only requires an email on first step, so I inputted my email and upon submitting the form I was sent an email saying I already had an account with them with an option to reset my password if I had forgot it. Upon clicking the link it redirected me to the homepage with the following:
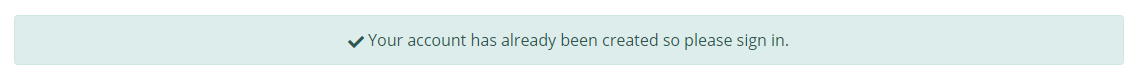
Weird. The button said “Reset password”, yet I was automatically logged into my account and it just redirected me to my profile. I went back to check what requests were made and this one stood out:
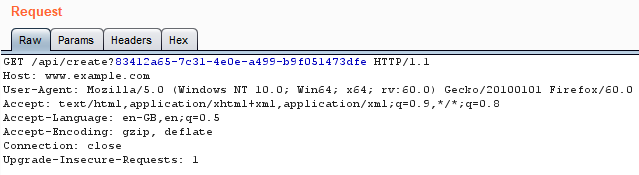
My first thought is: what happens if I re-visit this link? Sadly, it gave me a 404 error (tried on old session, still 404, figured token expired etc), however after submitting the register form above again, I visited the link again, except this time I tried it on a brand new session (unauthenticated). The result: logged into my account without entering my password!
So now i’m starting to think, is that value just the users id? Why does it not always work? Do we need to submit that form for the link to work? ..but if it IS my userid, how do we find another users id? I checked profiles, image urls, everything. I couldn’t find anything. Not wanting to give up, I decided to retrace my steps and to try find out where this parameter may be set (was it set in just the email via server side, or anywhere else?).
I quickly realised I should of paid more attention to what was in front of me. I submitted the form in Step 1 and inspected the HTML in closer detail. There in the the response right in front of me: :
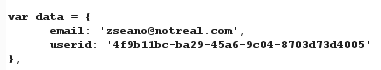
And there is the last piece to the puzzle. Our repo steps look like this:
- Submit users’ email you wish to takeover.
- Users ID will be in the response
- Visit the /api/create?userid and…. we’re in!
It is extremely easy to overlook such basic things, especially with so many different types of bugs to look for. Just take your time, understand your target, and understand what you’re trying to achieve. Stick to one thing at a time.
Until next time.. ;)
